lampiao
镜像在这里,是vulnhub提供的一个虚拟机,用VM打开之后便开始渗透测试。
主机发现
首先是主机发现,因为并不知道靶机的IP地址,于是使用nmap,进行扫描,这里我扫了vm虚拟网卡的C段nmap -sn 192.168.0.0/16,结果如下:
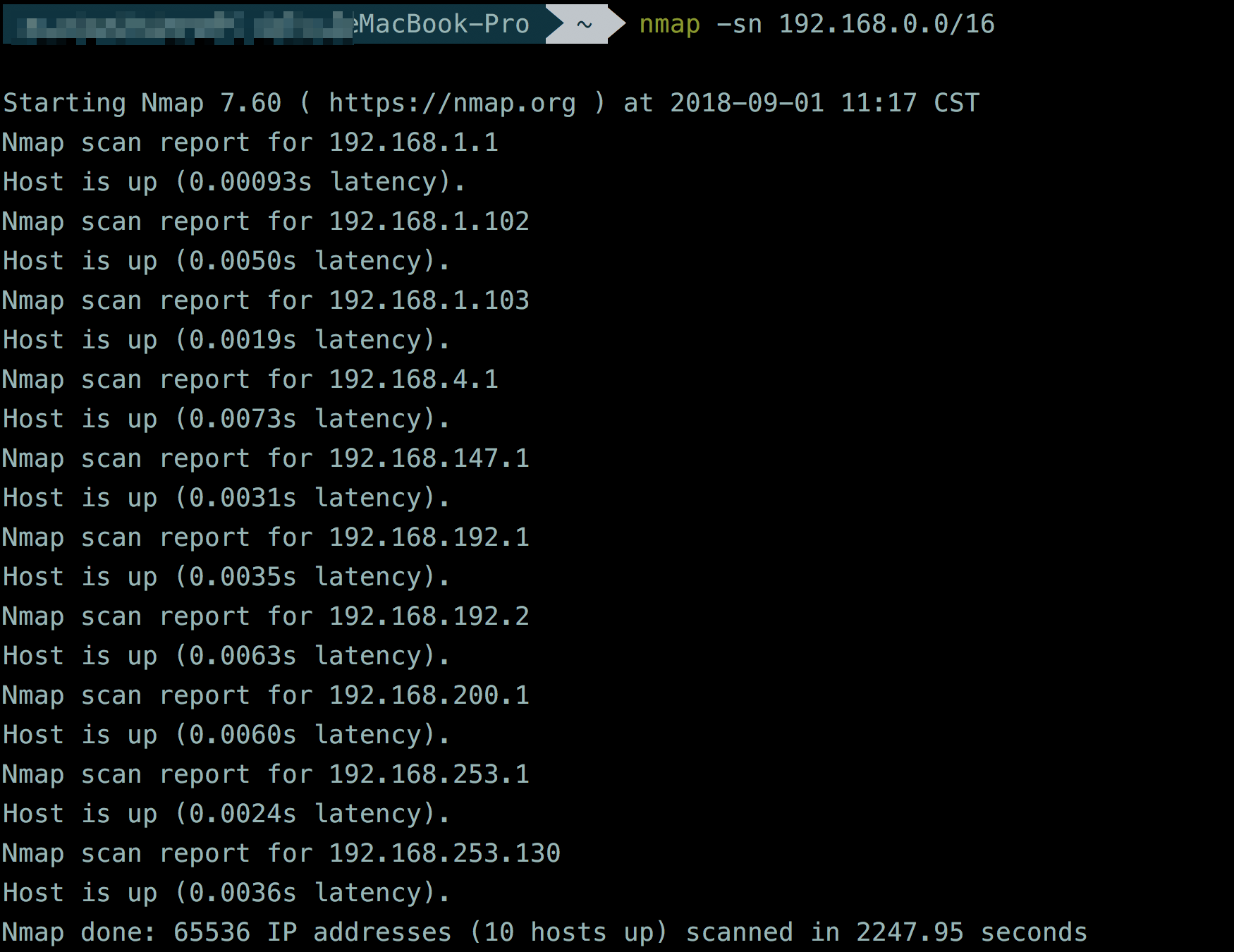
我们可以看到目标主机的ip地址应该是192.168.253.130这个。
端口扫描
之后对这个ip进行端口扫描(我将vm的网络模式改为了桥接模式,所以ip变为了192.168.1.100),首先扫了常见端口:
|
|
得到开放的两个服务,ssh和80端口的web。具体的ssh信息可以用msf的auxiliary/scanner/ssh/ssh_version进行探查:
|
|
没有得到什么其他有效信息,尝试用hydra进行密码爆破,用自带的字典没找到,使用crunch生成的字典也没有结果,目测行不通:
|
|
转看80端口web页面,是个静态页面,nikto扫了没什么发现,dirb和御剑扫目录,都没什么发现,emmmm尴尬。难道,服务放在了很脏的端口上吗? 于是重新进行了端口扫描,使用:
|
|
发现1898还开着一个web服务,有戏,访问看到:
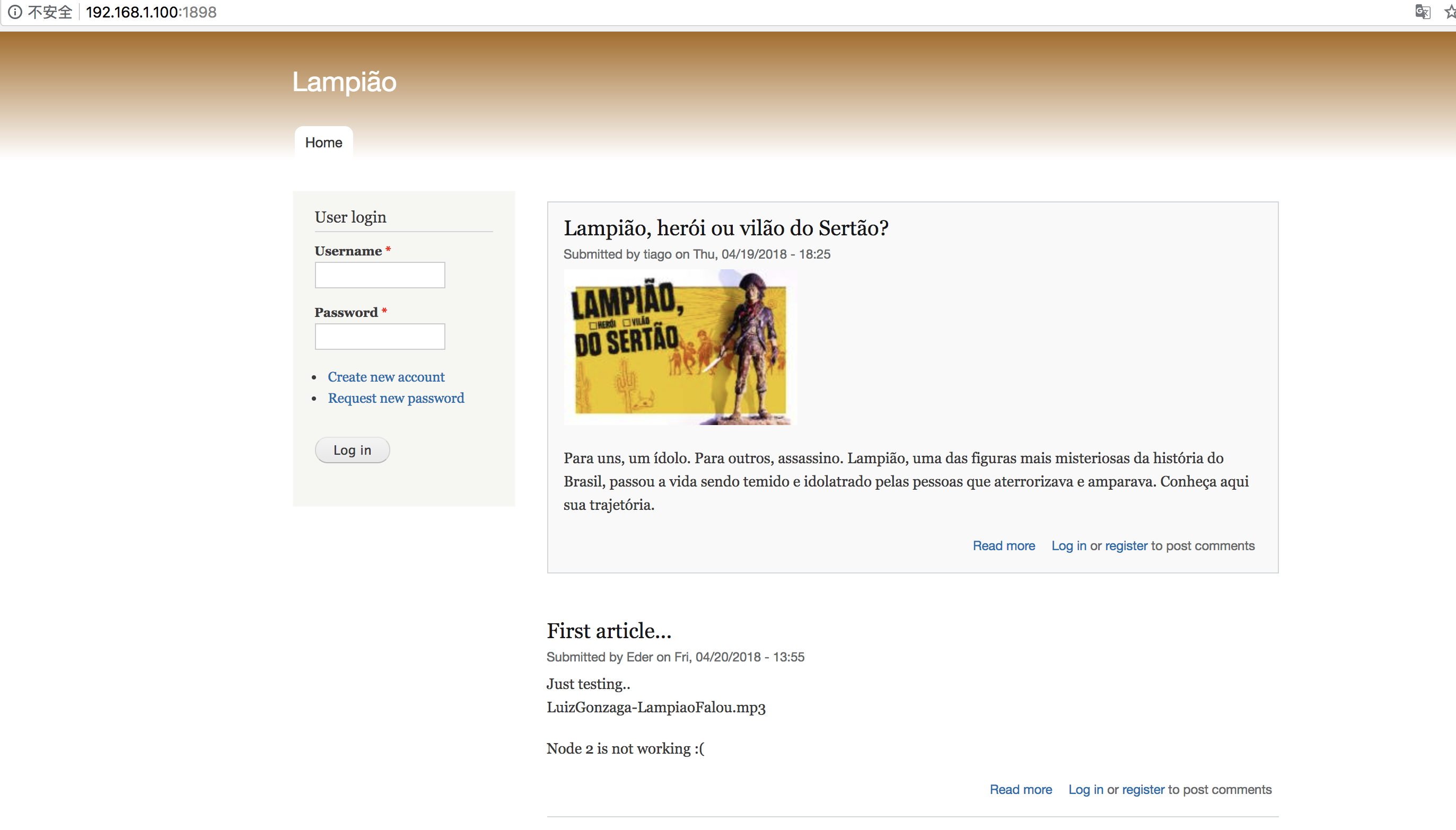
浏览一下页面,主页面只有用户登录、注册、找回密码等信息,推测可能存在的突破点:
- 页面sql注入
- 账号密码破解
- 目录扫描
- Drupal框架漏洞
我们预想去测试威胁比较大的框架漏洞,毕竟web常见漏洞比较繁琐,web页面如果多一时半会不太容易找到点。先扫下目录:
|
|
可以看见,扫到了一些目录和文件,摘出来可能有用的内容。/modules/路径可以看到其支持的组件,可能之后会派上用场,还有/robots文件,和xmlrpc.php可能会有用处。这里先大概扫一眼。
getshell
然后尝试对drupal框架进行攻击,我们查找drupal的漏洞:
|
|
这里,我们其实可以从刚才的robots.txt中看到其更新日志,为drupal 7.54 2017-02-01 所以,我们这里选了最新的drupal_drupalgeddon2,好像是才报的,我们使用info查看下详细信息,看来是CVE-2018-7600.去网上搜下这个漏洞的详情。Drupal CVE-2018-7600 分析及 PoC 构造
粗略的看了下,是一个远程代码执行漏洞,主要原理是drupal对于#开头的变量有特殊处理,在注册时,可以通过传入恶意代码,造成执行。
|
|
提权
得到shell,之后我们直接使用查看uname -a内核版本,我们首先考虑linux通用内核漏洞dirty cow:
|
|
于是之后我们使用CVE-2016-5195这个提权漏洞
/proc/self/mem
我们先利用的是这个
Linux Kernel 2.6.22 < 3.9 - ‘Dirty COW /proc/self/mem’ Race Condition Privilege Escalation (/etc/passwd Method)
这个显示的<3.9我一开始还以为无法使用,因为看到内核是4.4的,最后发现是可以的。漏洞具体的详情可以自己去看详情,这里不再赘述。我们首先下载exploit
|
|
便可以拿到root权限
PTRACE_POKEDATA
同样我们可以利用:
Linux Kernel 2.6.22 < 3.9 - ‘Dirty COW’ ‘PTRACE_POKEDATA’ Race Condition Privilege Escalation (/etc/passwd Method)
|
|
此时可以通过切换至firefart用户get flag。
FristiLeaks
镜像在这里,是vulnhub提供的一个虚拟机,用VirtualBox导入,注意这里需要将MAC地址修改为08:00:27:A5:A6:76
主机发现
这里我们换一个工具netdiscover,这个比nmap更为友好和快捷。
|
|
发现目标IP为192.168.1.100然后顺手查了下后面是个什么公司,竟然存在,先放着。之后端口扫描。有之前的教训,这次直接扫所有的。
端口扫描
|
|
emmm,只有80端口?别想骗我,换个姿势再试一下.emm还是没扫出来,那就先看这个好了。看下主页,一个静态页面啥都没用,扫目录。
|
|
有用的应该就robots.txt和cgi-bin,cgi-bin没权限,看下robots.txt好了,发现3个路径,cola、siisi、beer,访问了这3个发现都是图片.

冷静,冷静,图片有提示,fristi,虽然有点。。。但是也算进来了。一个登陆页面. 先看下源码,注释里面有一串内容,base64内容,解密后得到一个图片。
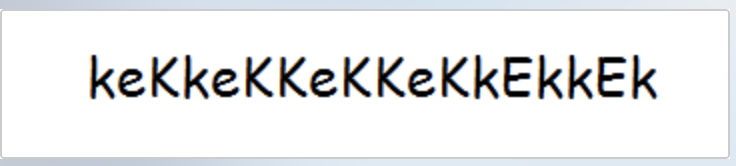
看起来是密码,与之前的eezeepz一起,尝试登陆。