HackingLab 题目比较基础,非常适合入门。
选择题
都比较基础,很简单,略过。
基础关
1.key在哪里?
直接看源码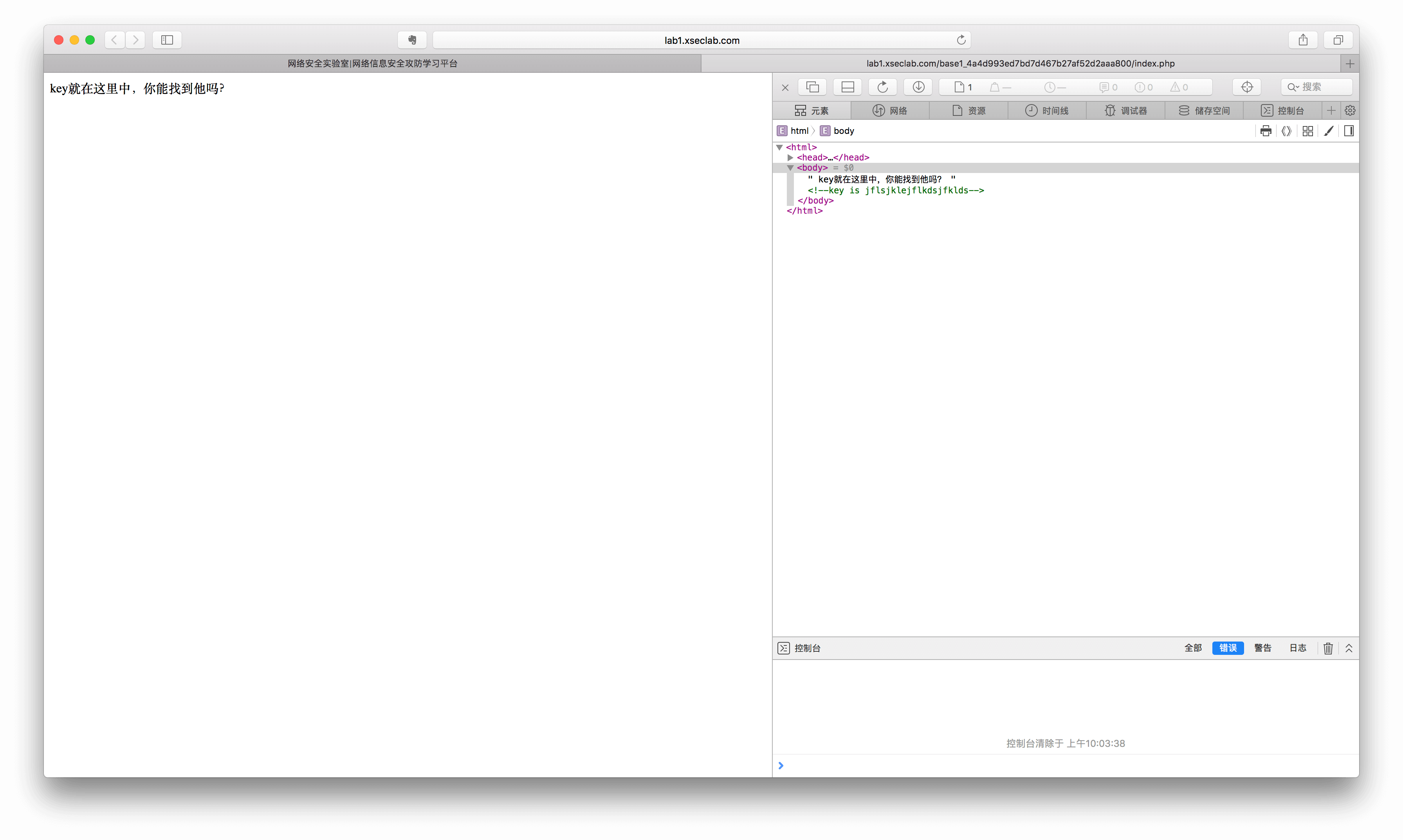
2.再加密一次你就得到key啦~
加密之后的数据为xrlvf23xfqwsxsqf
这里的知识点是ROT-13,密文加密后会得到明文,找个解密网站,得到key。
3.猜猜这是经过了多少次加密?
加密后的字符串为:
看得出来这是base64加密,写个脚本,不停解密直至报错。
|
|
4.据说MD5加密很安全,真的是么?
e0960851294d7b2253978ba858e24633
直接找个在线md5解密cmd5。
5.种族歧视
小明同学今天访问了一个网站,竟然不允许中国人访问!太坑了,于是小明同学决心一定要进去一探究竟!
跟国籍有关的只有Accept-Language,改成英文就可以: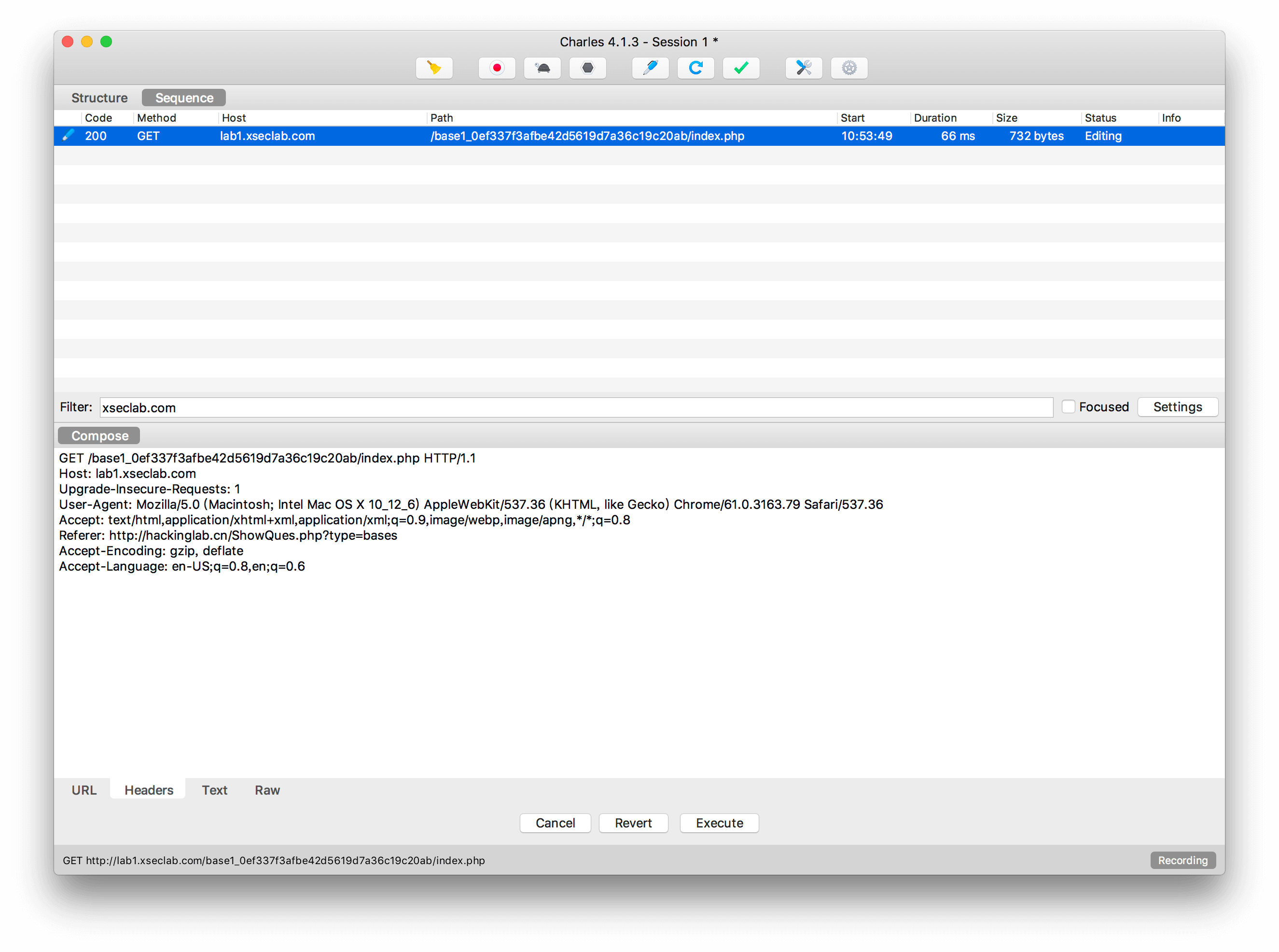
6.HAHA浏览器
据说信息安全小组最近出了一款新的浏览器,叫HAHA浏览器,有些题目必须通过HAHA浏览器才能答对。小明同学坚决不要装HAHA浏览器,怕有后门,但是如何才能过这个需要安装HAHA浏览器才能过的题目呢?
User-Agent字段代表了Request的浏览器类型,直接改成HAHA。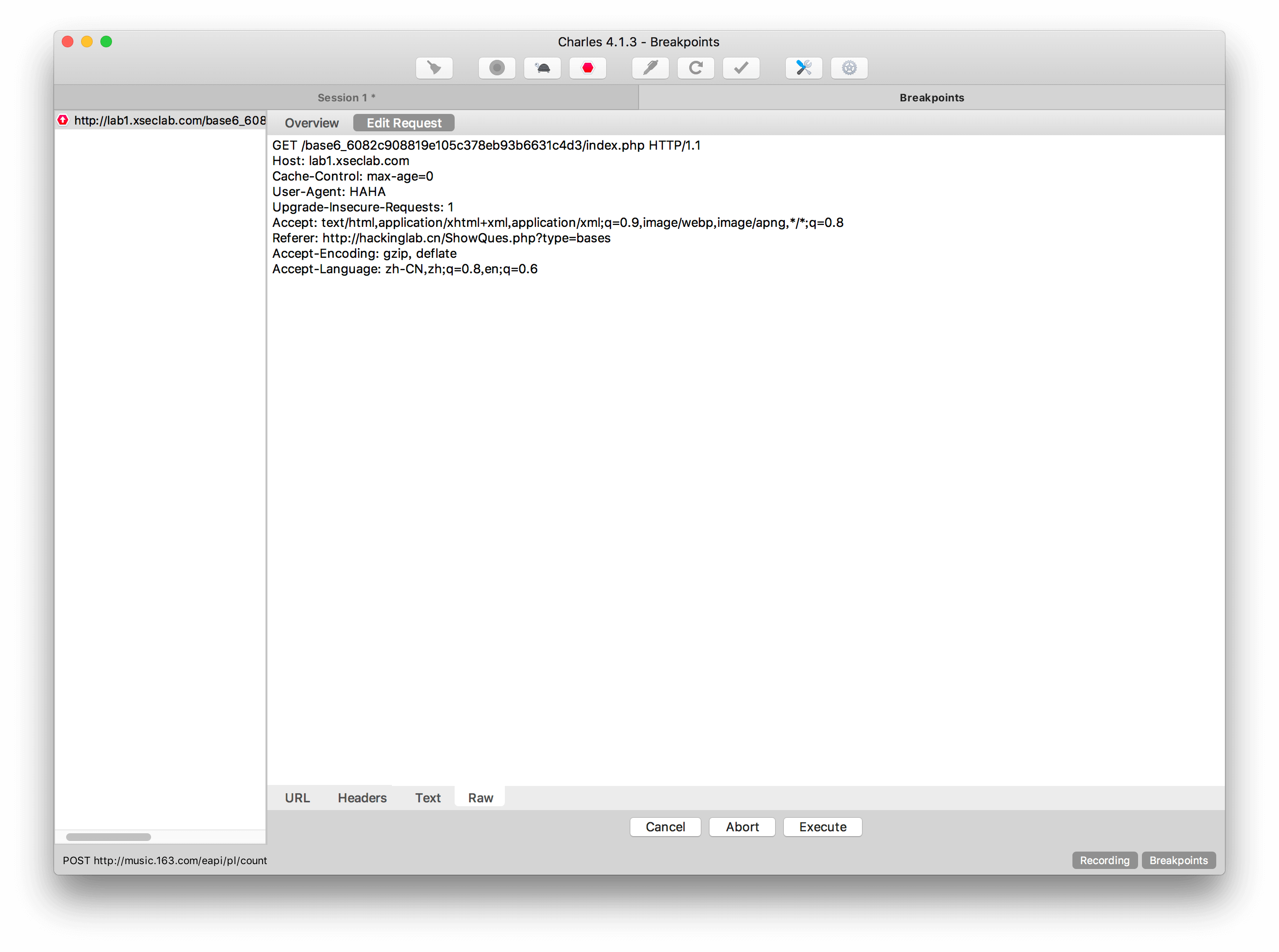
7.key究竟在哪里呢?
上一次小明同学轻松找到了key,感觉这么简单的题目多无聊,于是有了找key的加强版,那么key这次会藏在哪里呢?
抓包分析,看到Response头里面有key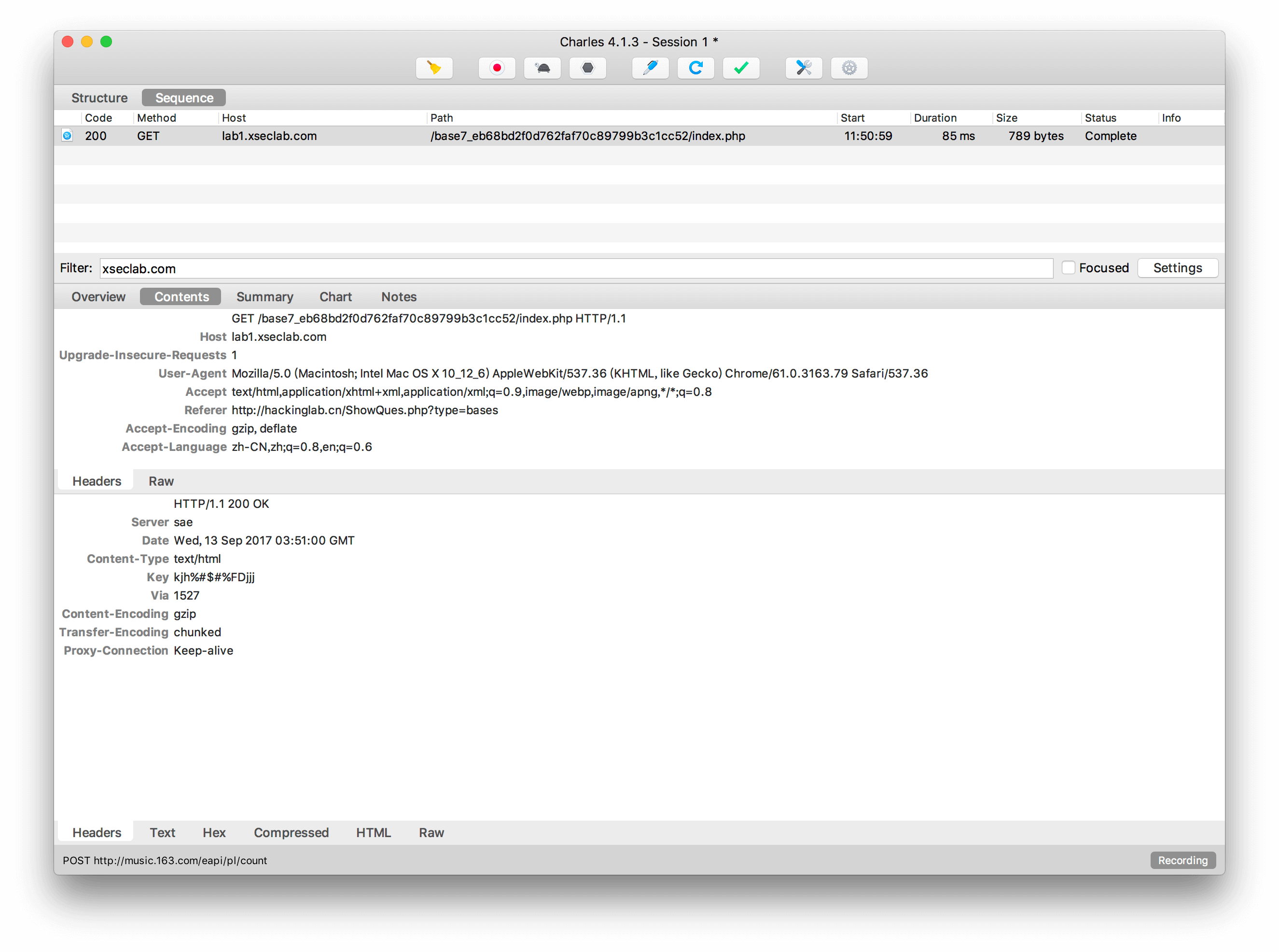
8.key又找不到了
小明这次可真找不到key去哪里了,你能帮他找到key吗?
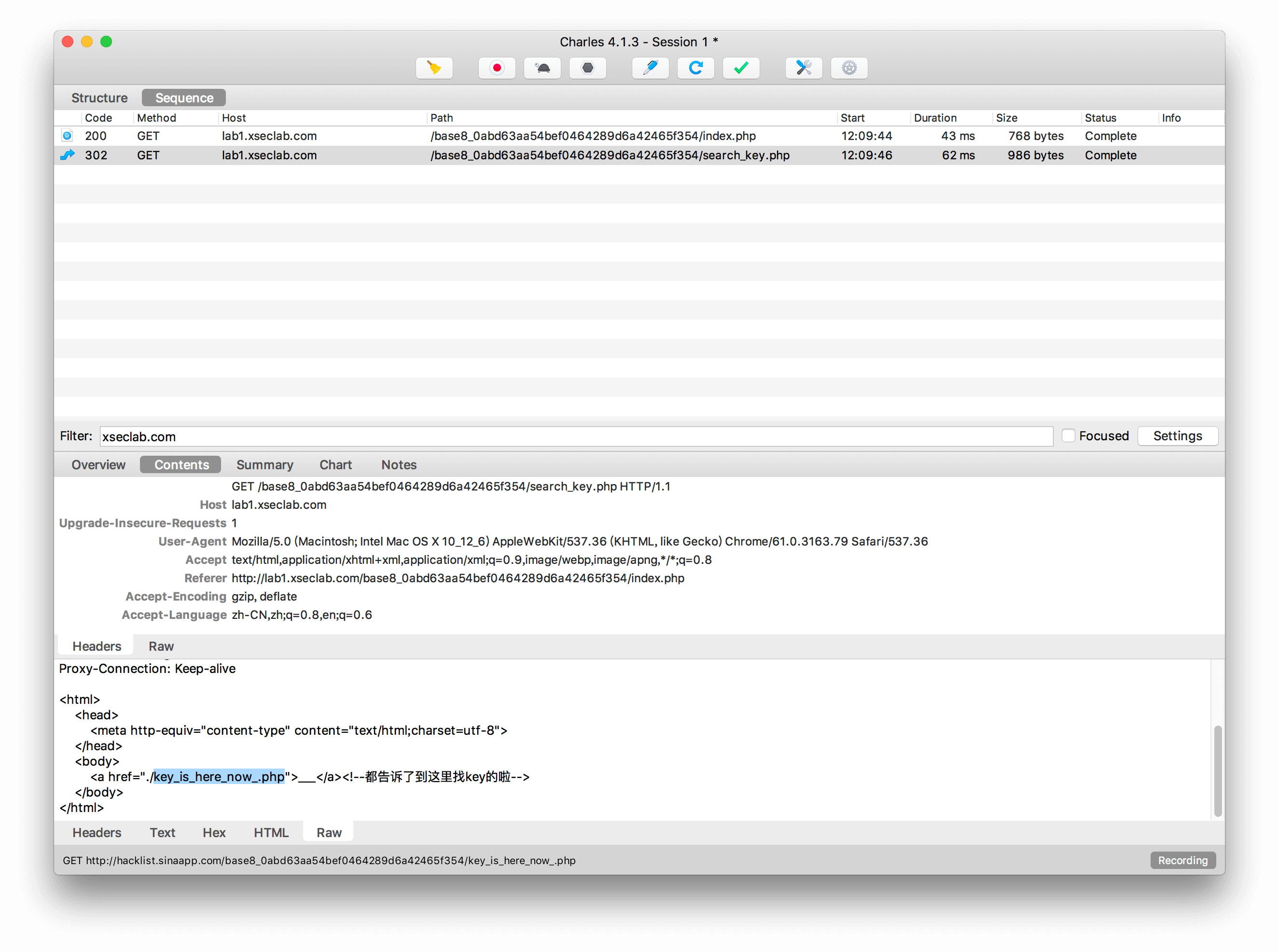
抓包发现302重定向,直接访问url。
9.冒充登陆用户
小明来到一个网站,还是想要key,但是却怎么逗登陆不了,你能帮他登陆吗?
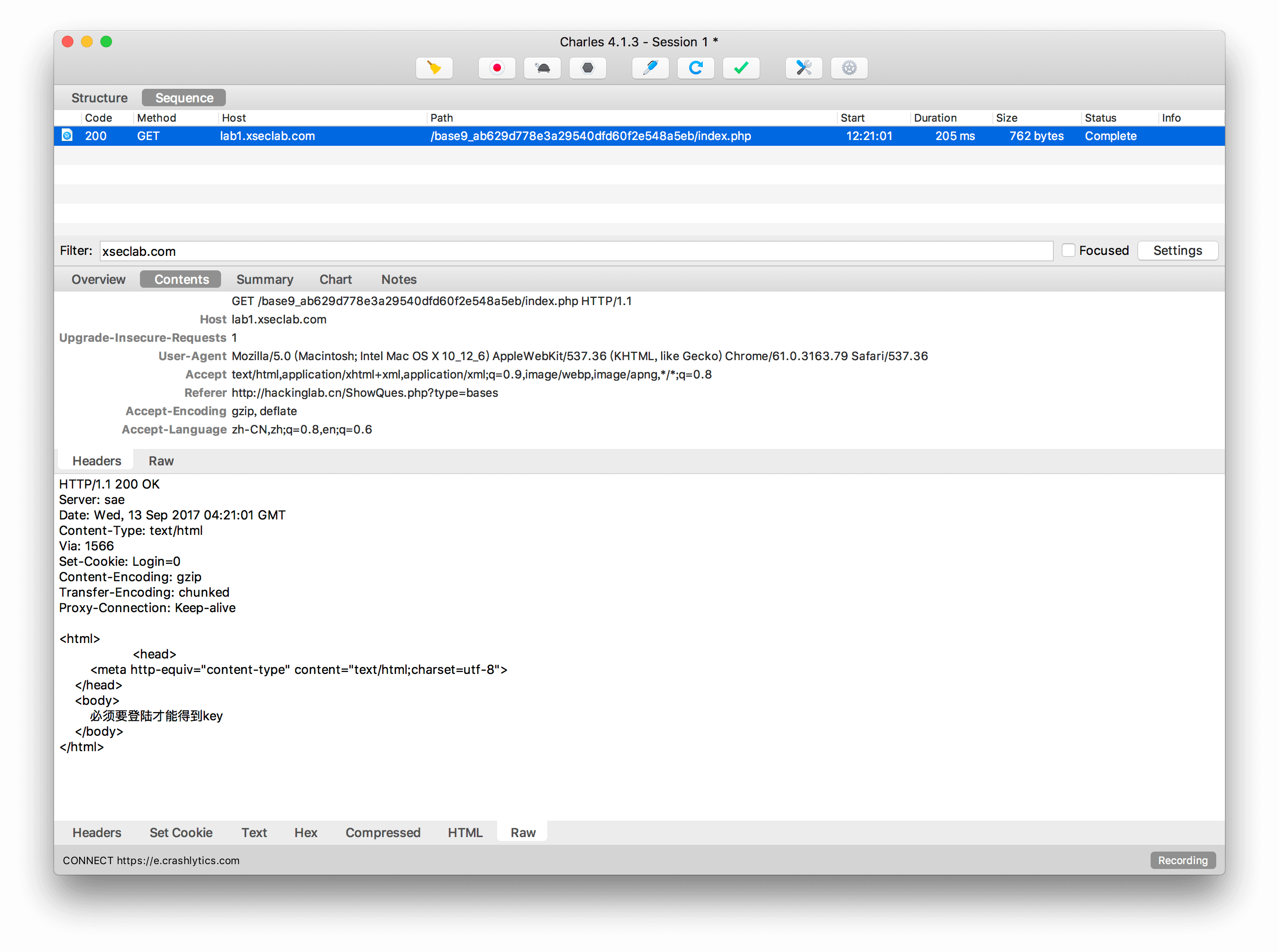
抓包发现Response头有个Set-Cookie: Login=0 重新发送Request 修改Cookie:Login=1即可
10.比较数字大小
只要比服务器上的数字大就可以了!
抓包分析,可以发现input设置了maxlength=3,猜测服务器估计跟1000比较,抓包直接修改RAW内容,随便填一个大数即可。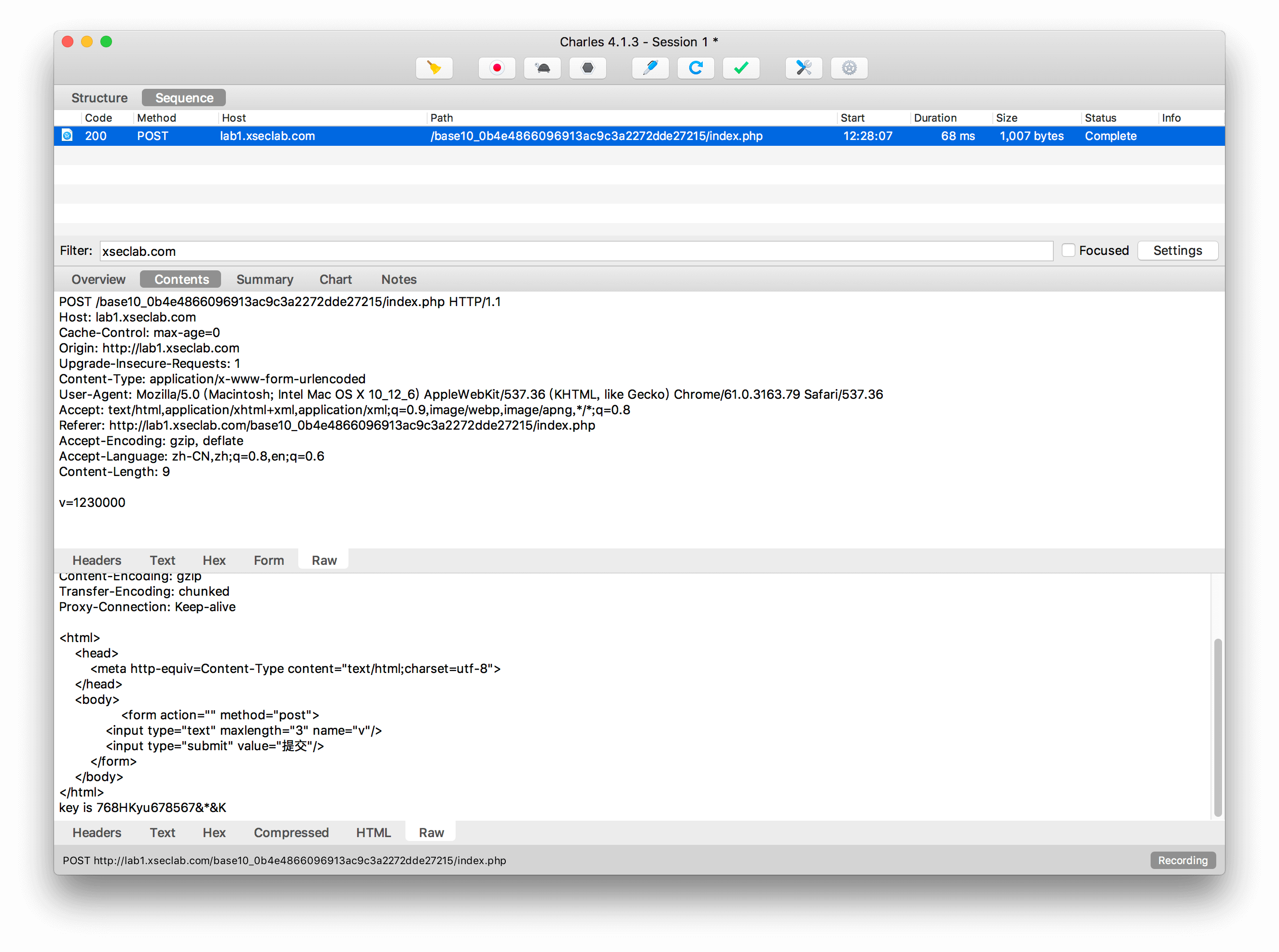
11.本地的诱惑
小明扫描了他心爱的小红的电脑,发现开放了一个80端口,但是当小明去访问的时候却发现只允许从本地访问,可他心爱的小红不敢让这个诡异的小明触碰她的电脑,可小明真的想知道小红电脑的80端口到底隐藏着什么秘密(key)?
添加X-Forwarded-For: 127.0.0.1 即可。
X-Forwarded-For是用来识别通过HTTP代理或负载均衡方式连接到Web服务器的客户端最原始的IP地址的HTTP请求头字段。
当今多数缓存服务器的用户为大型ISP,为了通过缓存的方式来降低他们的外部带宽,他们常常通过鼓励或强制用户使用代理服务器来接入互联网。有些情况下,这些代理服务器是透明代理,用户甚至不知道自己正在使用代理上网。
如果没有XFF或者另外一种相似的技术,所有通过代理服务器的连接只会显示代理服务器的IP地址,而非连接发起的原始IP地址,这样的代理服务器实际上充当了匿名服务提供者的角色,如果连接的原始IP地址不可得,恶意访问的检测与预防的难度将大大增加。XFF的有效性依赖于代理服务器提供的连接原始IP地址的真实性,因此,XFF的有效使用应该保证代理服务器是可信的,比如可以通过创建可信服务器白名单的方式。
12.就不让你访问
小明设计了一个网站,因为总是遭受黑客攻击后台,所以这次他把后台放到了一个无论是什么人都找不到的地方….可最后还是被黑客找到了,并被放置了一个黑页,写到:find you ,no more than 3 secs!
试了下常见的admin,发现没有,想到了一个东西robots.txt。
robots.txt是一种存放于网站根目录下的ASCII编码的文本文件,它通常告诉网络搜索引擎的漫游器(又称网络蜘蛛),此网站中的哪些内容是不应被搜索引擎的漫游器获取的,哪些是可以被漫游器获取的。因为一些系统中的URL是大小写敏感的,所以robots.txt的文件名应统一为小写。robots.txt应放置于网站的根目录下。如果想单独定义搜索引擎的漫游器访问子目录时的行为,那么可以将自定的设置合并到根目录下的robots.txt,或者使用robots元数据(Metadata,又称元数据)。
robots.txt协议并不是一个规范,而只是约定俗成的,所以并不能保证网站的隐私。注意robots.txt是用字符串比较来确定是否获取URL,所以目录末尾有与没有斜杠“/”表示的是不同的URL。robots.txt允许使用类似”Disallow: *.gif”这样的通配符。
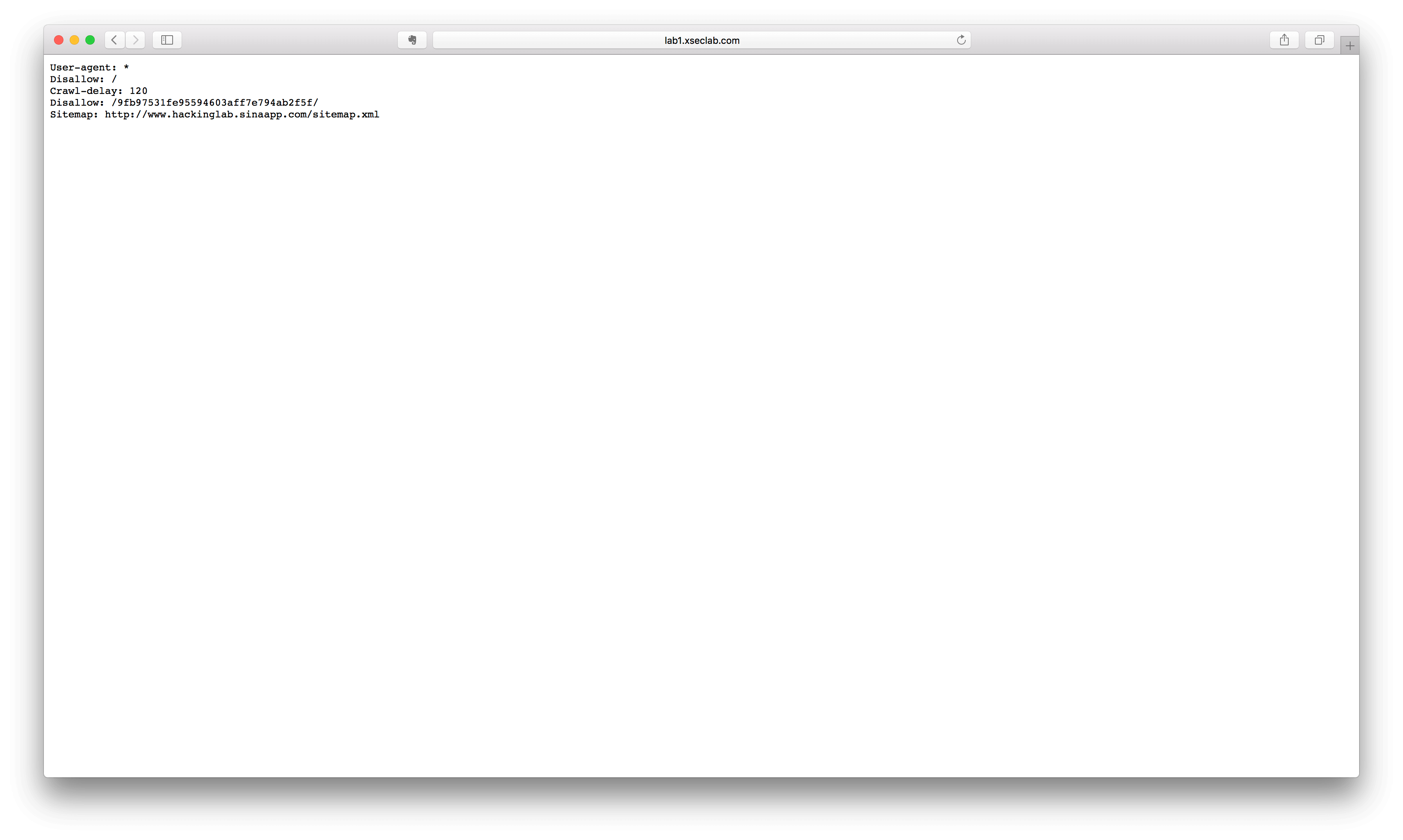
可以看见有个Disallow: /9fb97531fe95594603aff7e794ab2f5f/,访问这个地址发现说you find me,but I am not the login page. keep search.尝试login.php.get key.
脚本关
1.key又又找不到了
小明这次哭了,key又找不到了!!! key啊,你究竟藏到了哪里,为什么我看到的页面上都没有啊!!!!!!
抓包,发现有两条,中间那条即是key。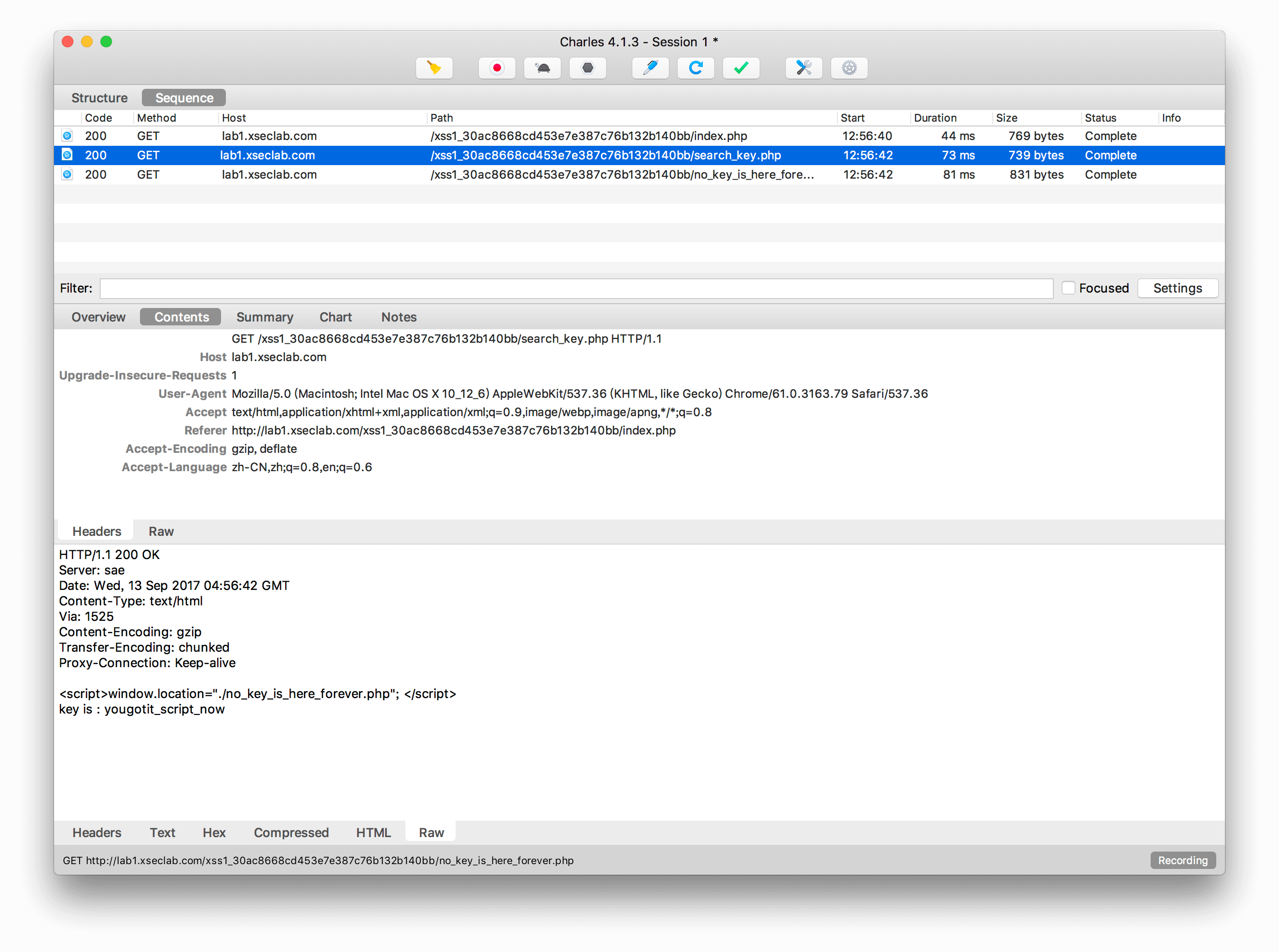
2.快速口算
小明要参加一个高技能比赛,要求每个人都要能够快速口算四则运算,2秒钟之内就能够得到结果,但是小明就是一个小学生没有经过特殊的培训,那小明能否通过快速口算测验呢?
发现每次的题目都不一致,只能上脚本了。
|
|
3.这个题目是空的
Tips:这个题目真不是随便设置的。 什么才是空的呢? 通关地址:没有,请直接提交答案(小写即可)
直接输出即可,尝试常见认为是空的字段,最后测得null。
4.怎么就是不弹出key呢?
提交说明:提交前14个字符即可过关
查看script,相关弹窗都返回false,直接拖到本地,删掉前面的:
|
|
剩下的运行就好了,因为要求前14个,改下输出:
5.逗比验证码第一期
逗比的验证码,有没有难道不一样吗?
验证码使用后不过期,上BurpSuite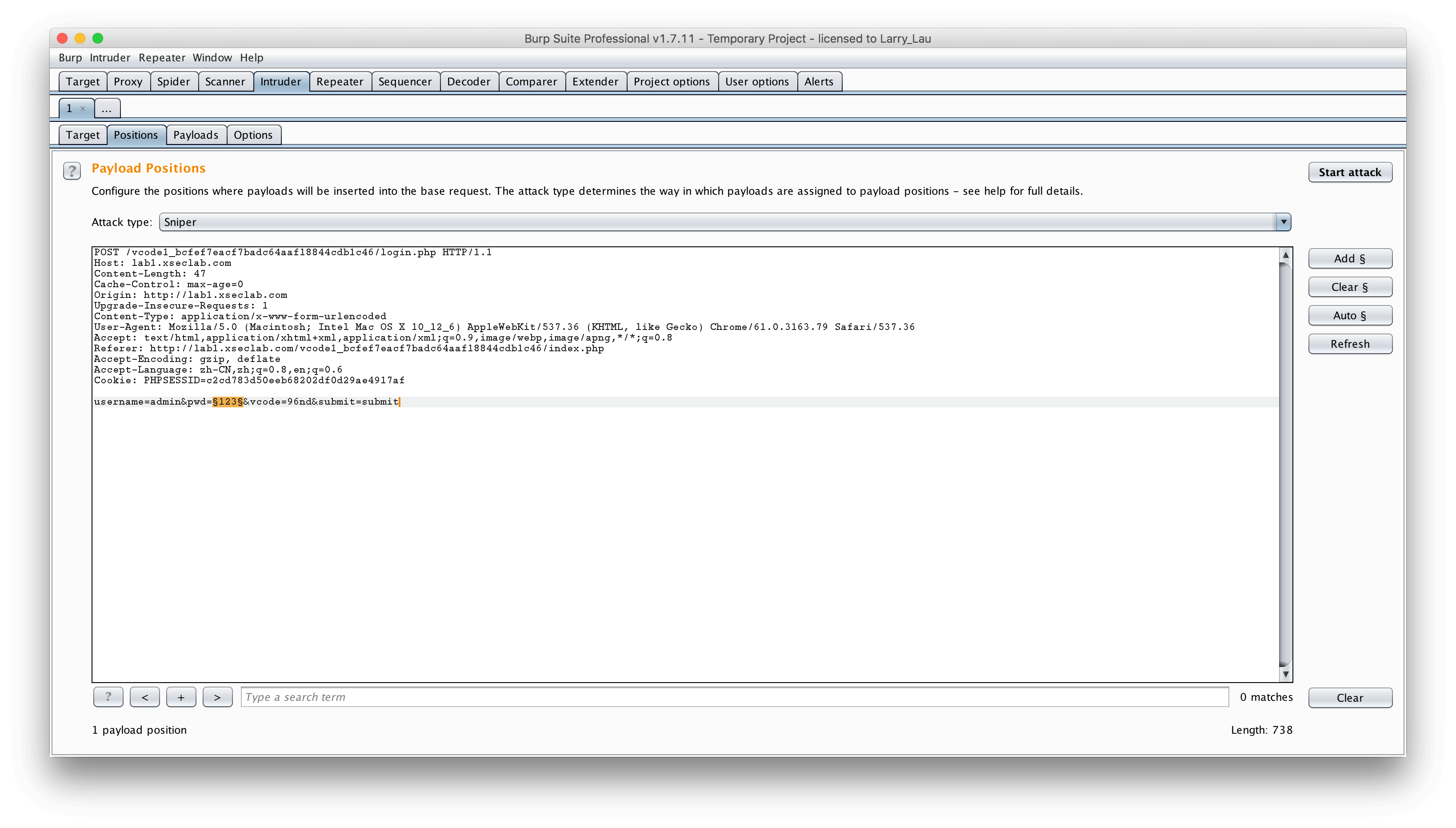
设置payload取值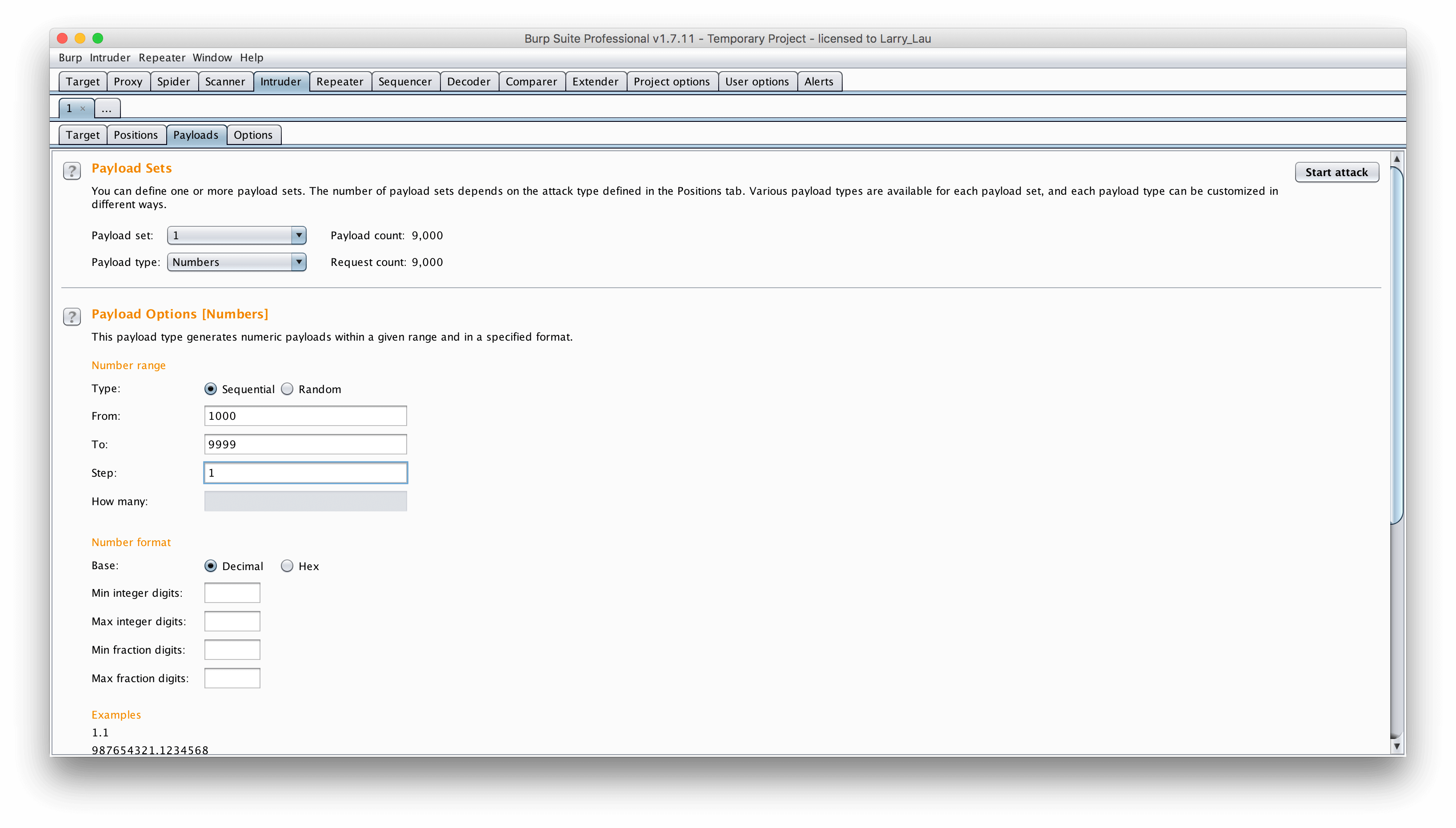
attack,根据length排序,发现有一个包不一致,得到key: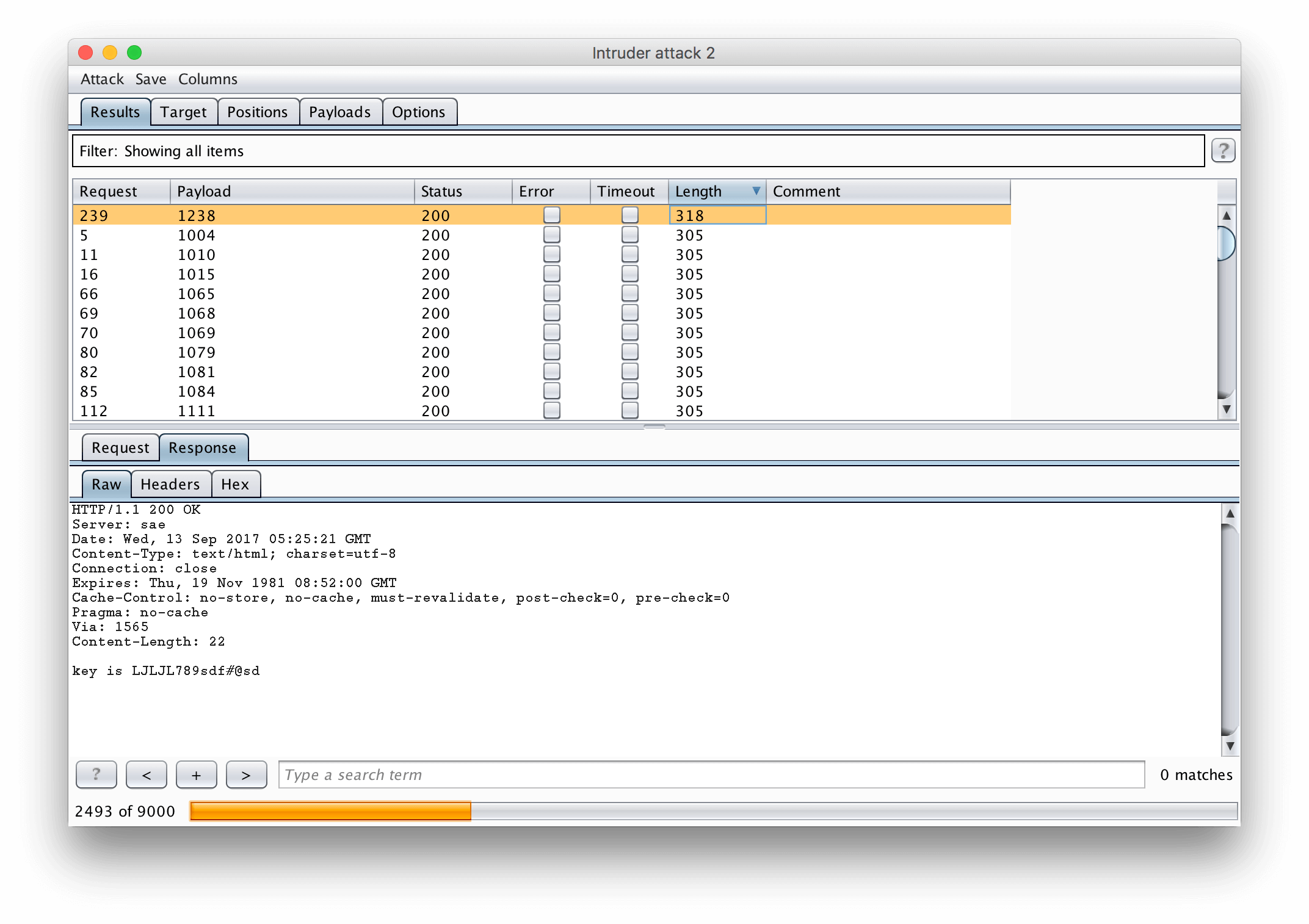
6.逗比验证码第二期
验证便失效的验证码
试几次就会发现他这个失效是真失效了,发的包不用加验证码了,直接去掉vcode字段进行破解。
7.逗比的验证码第三期(SESSION)
尼玛,验证码怎么可以这样逗比。。验证码做成这样,你家里人知道吗?
session验证,把 cookies 的内容删掉就好。
8.微笑一下就能过关了
尼玛,碰到这样的题我能笑得出来嘛…
看源码,发现源代码是一个链接,可以看到后台源码,点击看一下:
|
|
可以看到要使^_^字段满足所有内容才可以,算是一道php审计,需要知道一些知识。$_SERVER['QUERY_STRING']:QUERY_STRING就是URL后接的参数,如www.baidu.com/?a=b,a=b就是QUERY_STRING。
data伪协议:data:[<MIME-type>][;charset=<encoding>][;base64],<data>file_exists对data指向的内容判断为不存在
根据以上,可以得到^.^=data://text/plain;charset=unicode,(●’◡’●)即可得到key
9.逗比的手机验证码
你的手机号码是13388886666,验证码将会以弹窗的形式给出
点击获取验证码,然后不要submit,直接用13388886667和此验证码登陆即可。
10.基情燃烧的岁月
Tips:你是一名黑客,你怀疑你的“(男/女)闺蜜”的出轨了,你要登陆TA手机的网上营业厅查看详单,一探究竟! 闺蜜手机号码:13388886666
验证码获取之后一直有效,直接爆破,得到前任手机号,再爆破。
11.验证码识别
Tips:验证码依然是3位数
这里抓包尝试可以发现,获取手机验证码后,手机验证码答案是不变的,图片验证码验证一次后就失效,写脚本模拟操作,然后用图像识别进行验证码破解。注:图像识别可能不正确,需多试几次。图像识别这里使用了pytesseract,其依赖于tesseract,Mac可直接使用brew install tesseract进行安装。
|
|
12.XSS基础关
XSS基础:很容易就可以过关
什么都没过滤,直接<script>alert(HackingLab)</script>即可,注意chrome下会有xss 过滤器功能,需要关闭,不然会报错。在启动后面加上disable-xss-auditor即可,例如mac下进入/Applications/Google Chrome.app/Contents/MacOS中,执行./Google\ Chrome -args --disable-xss-auditor
13.XSS基础2:简单绕过
很容易就可以过关.
没什么说的,基本操作<img src=1 onerror=alert(HackingLab)>
14.XSS基础3:检测与构造
alert' onmouseover="alert(HackingLab)"
15.Principle很重要的XSS
原理/原则/理念很重要…..不是所有的xss都叫特仑苏.. ^_^
Take it easy!
常规方法没想到,有个取巧的办法,直接拦截response包然后加上<script>alert(HackingLab)</script>即可
注入关
1.最简单的SQL注入
发现提示是login as admin,直接构造admin' or '1'='1即可
2.最简单的SQL注入
提示id,说明key应该在某个id的页面中,直接id=1 or 1=1即可
3.防注入
试过常见闭合方式之后无效,尝试宽字符注入
|
|
发现正常显示,即发现注入点。然后是一般流程:
得到字段数:
|
|
发现到4时有问题,所以返回字段数为3。
得到显示位置:
|
|
发现显示2,3,所以第2、3字段的内容被显示出来,之后注入时可以通过将内容放在这两个位置上以便观察
得到所有数据库和当前数据库:
|
|
可以看到,总共有3个数据库information_schema,mydbs,test,当前使用的数据库是mydbs
得到表名
|
|
可以看到,mydbs数据库中只有一个表sae_user_sqli4
得到字段
|
|
注意table_name需要使用hex()函数将字符串转为16进制数,因为'被转义了。最终得到了字段id,title_1,content_1
脱裤
|
|
获取记录条数,总共4条。
获取所有内容如下:
blog systemmy blog test,so easyeasy ,flagishere#Hsaagdfs56sdf7fsdv,where is flagflag is here!
得到flag
4.到底能不能回显
小明经过学习,终于对SQL注入有了理解,她知道原来sql注入的发生根本原因还是数据和语句不能正确分离的原因,导致数据作为sql语句执行;但是是不是只要能够控制sql语句的一部分就能够来利用获取数据呢?小明经过思考知道,where条件可控的情况下,实在是太容易了,但是如果是在limit条件呢?
首先尝试正常修改start和num值,发现num不会改变最终结果,尝试start=5 or 1=1&num=5时,会显示:
|
|
发现number无效时好像会显示第一个。题目提示了limit注入,所以SQL语句应该是这样的:
|
|
由于union无法在order by语句后面,通过查看select用法,可以知道后面还有procedure和into outfile,后者这里无法利用,则尝试使用procedure MySQL默认只有analyse(),analyse的用法在这里。
|
|
尝试:
|
|
看到返回 Can't use ORDER clause with this procedure,说明无法使用,尝试在analyse函数中构造错误,通过返回错误显示来得到结果,修改analyse中的参数,尝试在参数中使用语句:
|
|
发现不行,报错
最后根据这篇文章,发现可能extractvalue这个函数可以使用,查看extractvalue发现他是用于xml解析,尝试构造,随便填两个字符串
|
|
返回XPATH syntax error:,发现报错注入
|
|
返回XPATH syntax error: '.73',发现显示不全,想办法在之前就开始报错,修改内容使其更好显示,这里使用concat进行查看
|
|
可以看到最终错误显示了出来,之后就是正常步骤了
得到当前数据库
|
|
XPATH syntax error: ‘%mydbs’
得到表名
|
|
XPATH syntax error: ‘%article,user’
注意要将语句用()括起来,不然会报语法错误。由此得到,此数据库中有2个表:article和user
得到列名
|
|
XPATH syntax error: ‘%id,title,contents,isread’
XPATH syntax error: ‘%id,username,password,lastloginI’
分别得到每个表的字段值
得到内容
查表user发现有3个记录,id为1,2,12889,且12889的username为flag,尝试获取其password值
|
|
XPATH syntax error: ‘%myflagishere’
5.邂逅
小明今天出门看见了一个漂亮的帅哥和漂亮的美女,于是他写到了他的日记本里。
这题不一样的地方就是注入点不在原始url上,而在图片url上,且是宽字符注入,知道这点基本就算成功了。
得到字段
|
|
得到字段为4个,然后查看显示位:
得到显示位
|
|
这里用charles抓包显示,看到显示位为3
得到数据库名
|
|
得到表名
|
|
article,pic
得到字段
|
|
article的字段: id,title,content,otherspic的字段: id,picname,data,text
得到内容
|
|
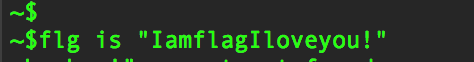
得到图片库1dog1.jpg,2cat1.jpg,12998flagishere_askldjfklasjdfl.jpg,发现有个flag.jpg,尝试askldjfklasjdfl无效,访问图片的到IamflagIloveyou!
6.ErrorBased
本题目为手工注入学习题目,主要用于练习基于Mysql报错的手工注入。Sqlmap一定能跑出来,所以不必测试了。flag中不带key和#
首先测试,发现有错误返回
提示说是报错注入,尝试一下看看结果
发现成功看到结果,之后就是常规操作了。关于报错注入,可以看这里的总结。
获取数据库名
|
|
获取表
|
|
注意这里不要用group_concat(table_name)而要一个一个去获取,最终得到log、motto、user三个表
获取列
|
|
最后得到id、username、motto
这里发现 在之后使用 select motto from mydbs.motto时无效,进而放弃,选择报错注入的另一种,利用XPath报错。
|
|
发现好像显示不全,只能一个个查看,limit 3,1时得到结果。
7.盲注
今天我们来学习一下盲注.小明的女朋友现在已经成了女黑阔,而小明还在每个月拿几k的收入,怎么养活女黑阔………..so:不要偷懒哦!
|
|
可以看到延时了很久才返回,说明成功。这里手工注入太累,网站网速又慢,用sqlmap跑吧。
|
|
ps: 原理知道了就好了,那个网站网速太慢,sqlmap经常连不上。
8.SQL注入通用防护
小明写了一个博客系统,为了防注入,他上网找了一个SQL注入通用防护模块,GET/POST都过滤了哦!
这里常见的url注入都不起作用。最后搜索发现注入点在cookie上,需要以这种形式才能够成功:Cookie:PHPSESSID=xx;id=2 这里id后面的就是注入点。
|
|
后面就是基本操作了
9.据说哈希后的密码是不能产生注入的
查看源代码,发现关键语句
|
|
这里发现userid使用intval转为数值了,后面passwd使用md5hash之后进行拼接,这里主要是利用了php md5()函数可以返回 RAW MD5的方式具体如下:
|
|
这是php md5函数的文档,可以看到,当第二个参数设置为true时会返回16字节长度的原始二进制格式内容,默认返回的是32位 hex字符串,
Raw MD5 hashes are dangerous in SQL statements because they can contain characters with special meaning to MySQL. The raw data could, for example, contain quotes (‘ or “) that would allow SQL injection.
即如果我们的查询语句是:
|
|
通过构造raw_md5值可以变成如下:
|
|
又由于mysql会将'1<shit>'这样的string转换成booltrue,从而使的注入成功。
所以我们需要找到某个字符串,其MD5值插入后是这样的:
|
|
||和or相同,OR oR等内容,1的值可以为任意值。
还有一个解法就是如果RAW MD5包含'xx'='xx',即:
|
|
这种格式也可以,因为'a'='b'='c'会被转换成1,原因如下:
‘a’=’b’=’c’ is evaluated in this order : (‘a’=’b’)=’c’.
As ‘a’ != ‘b’, ‘a’=’b’ gives us 0, and that leads us to the final comparison 0=’c’. Then, MySQL tries to cast ‘c’ as a number, and finds 0.
The comparison is now : 0=0, which finally gives us 1.
所以最后附上我写的搜索程序:
|
|
也可在此基础上进行修改,优化,添加更加宽松的条件,会搜索的更快。
上传关
1.只能上传jpg格式的图片哦~!
查源码,发现在本地校验的,直接抓包修改后缀即可。
2.请上传一张jpg格式的图片
同上
3.请上传一张jpg格式的图片
文件名改为a.jpg.php即可
解密关
1.以管理员身份登录系统
以管理员身份登录即可获取通关密码(重置即可,无需登录)
补充说明:假设除了admin用户,其它用户的邮箱都可被登录获取重置密码的链接。
看了一下题目,补充说明说除了admin用户 其他用户邮箱都可以被访问,尝试重置用户admin发现没有链接,尝试重置其他任意用户xxx,发现会跳转至一个页面并提供了一个重置密码的链接,点开之后显示重置成功,这里发现重置成功的链接:
|
|
发现url中有用户名,猜测应该是通过更改url参数从而实现admin账号密码重置。
尝试直接修改username=admin发现不行,尝试了几个不同的非admin账号,发现sukey字段也不一样,相同的账号每次也不一样,猜测可能是类似账号密码加salt的哈希值之类的,尝试一下常见的hash破解,发现md5值,且原内容为1508842257,不是我们猜测账号密码之类的东西,电话也不对,位数不够,突然想起来是时间戳!
所以猜测整个重置流程会将发送邮件时候的sukey=时间戳和username一起作为验证信息来判断,从而进行重置,那就简单了,点完admin重置之后获取下时间戳然后求MD5加进去,注意要改成小写,大写好像不行,即可。